Authored By Jeff Bathurst | Director, Technology Advisory
Cybersecurity has never been something that businesses could ignore. Since the dot-com boom of the 1990s brought the world online, cyber-attacks have only become more advanced and widespread with each passing year. Unprecedented events like the Covid-19 pandemic, contested political elections, and increased social and political unrest have only led to an acceleration in the number and severity of cybercrimes.
In 2021, we saw the largest and most sophisticated cyberattacks in history. The Solarwinds attack, for instance, remained undetected for months and, in that time, infected over 18,000 businesses, including nine federal organizations. The good news is that any of these attacks could have been prevented with a defensive approach to cybersecurity. A proactive versus reactive strategy will be required to keep data and systems secure in 2022 and beyond.
#1 Cloud Vulnerabilities
The cloud is the future of IT. Each year, more businesses move their outdated IT infrastructure to a cloud provider for many reasons, including but not limited to:
- The cloud makes a company’s data and applications available on the internet, enabling remote work capabilities
- It reduces the cost and hassle of IT by outsourcing the hardware and the staff to maintain it
- The cloud is typically more secure than on-premises data centers
However, the security of a cloud environment depends on using best practices when configuring and maintaining it, and unfortunately, not every business is doing so. In fact, Verizon’s Data Breach Investigations Report found that over 90% of the 29,000 breaches analyzed were web app breaches, and IBM found cloud vulnerabilities increased by 150% in the last five years.
Migrating systems to the cloud is more than just relocating them. To take advantage of what can be a more secure environment, a business must upgrade its security practices along with upgrading its infrastructure.
#2 Remote Work Environments
When the Covid-19 pandemic swept the US, many businesses had to transform their workforce into a remote one overnight. Some were prepared. Others are still making changes while they are becoming familiar with the cloud-based infrastructure required for remote work. Cloud environments make conducting business easier, but gaps in cloud security still exist. Consequently, the distributed nature of remote work gives hackers more access to these gaps. According to DarkReading, businesses suffered from 50% more cyber-attacks in 2021 than they did the year before, and the trend is continuing upward.
Average Weekly Attacks per Organization by Industry (2021)
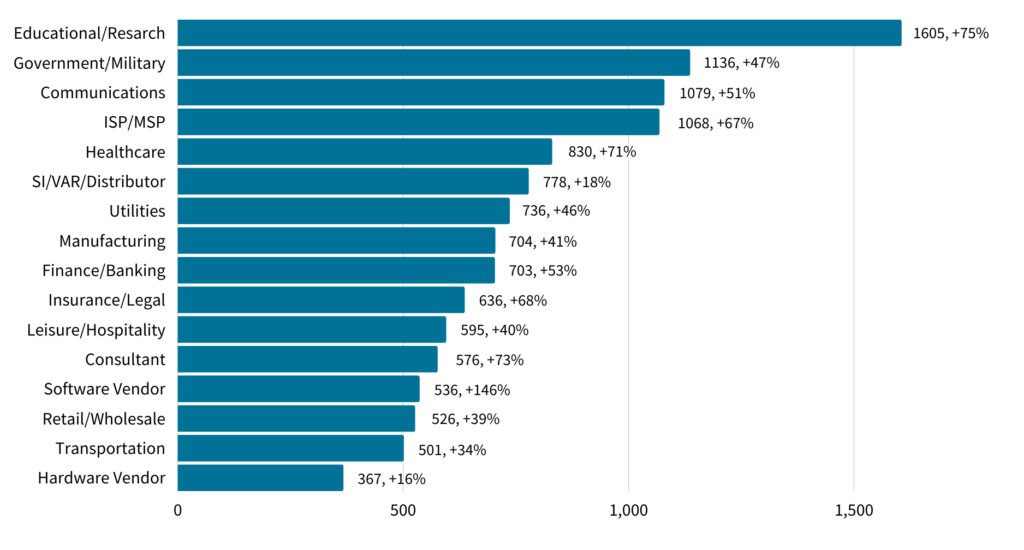
Employees need to be aware that they are more vulnerable to cyberattacks while working remotely. Attackers are using the fact that remote workers regularly have to update the software themselves, click on Zoom links for meetings, and give IT staff remote access to trick them into doing the same with spoofed emails and chats. This can result in malware infecting the employee’s device and potentially the entire network. Vigilance is necessary, and every communication should be verified before clicking any links.
Luckily, this trend can be stopped. Employee security training, increased cybersecurity measures, and intimate knowledge of cloud security controls can make remote work more secure than working in the office, but it requires a business to be proactive.
#3 Geopolitical Events
Cyber threats were a big enough problem when hackers were criminals that acted on their own. That is no longer the case. Both the Chinese and Russian governments have sponsored hacking groups to compromise the computer networks of governments and businesses around the world. The United States is one of its favorite targets, and Russian-based cyberattacks on US businesses have increased since the Russian invasion of Ukraine.
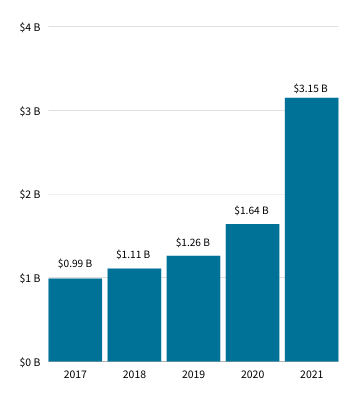 Because of this surge in attacks, cyber insurers are cracking down by raising rates. According to the Wall Street Journal, direct-written premiums collected by insurance carriers in the US in 2021 inflated by 92% year-over-year—a direct reflection of these higher rates.
Because of this surge in attacks, cyber insurers are cracking down by raising rates. According to the Wall Street Journal, direct-written premiums collected by insurance carriers in the US in 2021 inflated by 92% year-over-year—a direct reflection of these higher rates.
To keep up with the increased attacks, both companies and individuals must be motivated. There are new threats almost daily, but ongoing training can prevent them from affecting your business. Knowledge of the threats will allow your business to update your cybersecurity strategy, establish new protocols, and add more employee training to account for these threats and to stop them before they harm your business.
#4 The Covid Pandemic Continues
Scammers like to take advantage of calamities and the uncertainty they create. The Covid-19 pandemic gave cybercriminals a new tool that they could use to prey on people’s fears with phishing schemes, spoofed websites, and other techniques to steal their data and credentials. Despite governments around the world rolling back restrictions, the pandemic is not over yet. Regardless of this situation, these attacks can still be prevented.
Most cyberattacks that involve malware, phishing, or spoofing are only successful because of human error. People are more easily tricked when they are uncertain about the future, and the best way to prevent your business from falling victim to these types of attacks is by training your employees. Employees are less likely to fall victim to scammers’ tricks when they:
- Are aware of prevalent threats
- Know how to look for red flags
- Pay attention to details
- Report suspicious activity
#5 Rise in Ransomware Attacks
One of the most devastating types of cyber-attacks is the ransomware attack, which is not something that any business can afford to ignore. These attacks make it impossible for a company or government agency to do business by locking up its data and systems until a ransom is paid. Ransomware attacks boomed during the pandemic and show no sign of slowing down. They have caused many businesses to pay out millions of dollars and others to declare bankruptcy.
With ransomware on the rise, inaction is not an option. Every business is at risk. While having insurance used to be a good backup plan for a ransomware attack, the recent crackdown on cybersecurity insurance renewals has made prevention the best line of defense.
Conclusion
There is no way around it. Doing business in today’s digital world requires a strategic cybersecurity plan. Without one, a business is trying to hide in plain sight from hackers who know technology inside and out. Hackers are experts at what they do, and to stop them, a business needs the proper cyber hygiene along with the appropriate protection and training and an adequate post-attack procedure.
The first step to protecting a business’s systems and data from cyber-attack is knowing where you stand. A cybersecurity readiness assessment will show you how prepared your business is to defend against cyber-attacks and the steps you need to take to prepare for the inevitable.