Authored by Jeff Bathurst & Anthony DiGiulian
There is no question that the Covid-19 pandemic has and continues to disrupt businesses, effecting permanent changes to the way we work. Many companies have since continued operating either a remote or hybrid work environment, requiring an increase in technology which poses significant repercussions when it comes to cybersecurity. This has left many organizations contemplating the question, “Now that my employees are working from home, how do we keep our data and information secure?”
Why Remote Work Increases Cybersecurity Risks
A remote work environment can be just as secure as working from the office, it just requires preparation and awareness.
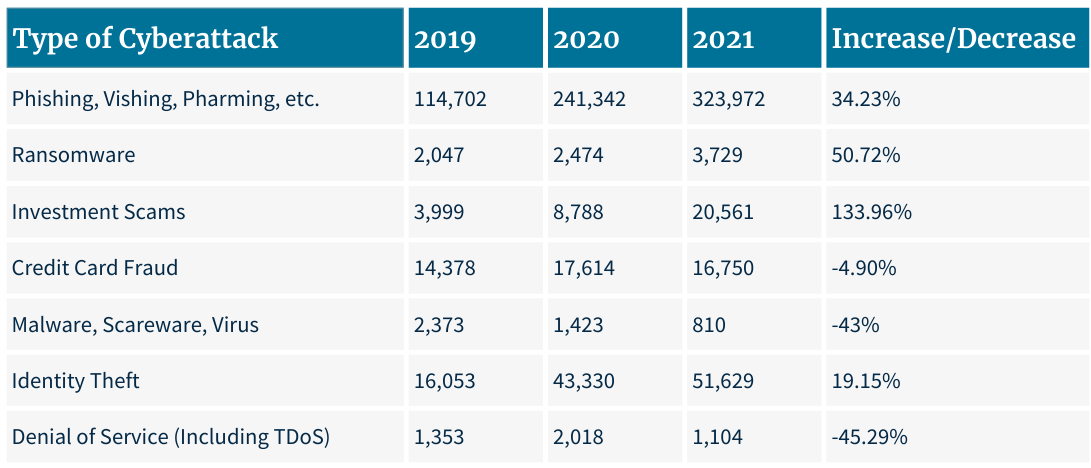 FBI.gov 2021 Internet Crime Report
FBI.gov 2021 Internet Crime Report
Despite rises in cyberattacks, many companies feel that hybrid or remote work is a win for both employees and organizations. To keep your organization operational and protected, the common security risks inherent in remote work need to be considered and addressed:
- Unclear, unenforced, or out-of-date cybersecurity policies
- Inadequate monitoring and examination of cyber threats
- Lack of employee cybersecurity training
- Increased distractions that can turn into cybersecurity threats
- Strained infrastructures and systems that lack capacity and computing power
- Points of entry/attack vectors are multiplied through more online activity
With the proper cybersecurity practices, all these risks can be mitigated.
Best Practices for Cybersecurity and Remote Work
The first steps in assessing your organization’s cyber posture are to identify current practices and protocols, understand what is or isn’t working, and find the gaps that need to be filled. Whether operating in a remote/hybrid workforce or not, these best practices will strengthen security and foster ongoing awareness.
# 1 Employee Awareness
Humans are the weakest link in the cybersecurity chain. When they are at work, they are focused on getting work done, not on cyber threats. With the shift to remote work, employees had to adopt new technologies, like video conferencing and instant messaging tools, almost daily, and this took even more of their focus. Humans are not good with change, and cyber threat actors are aware of this fact.
Beware of Employee-Directed Attacks
Most cyberattacks can’t happen without human error. Phishing attacks are only successful because people open emails when they shouldn’t. Many malware infections are effective because someone hastily downloaded a file without doing due diligence.
But can you really call it “human error” when employees aren’t aware of the risks they face daily? According to Cybertalk.org, 83% of organizations reported phishing attacks in 2021. It’s predicted that in 2022, an additional six billion attacks are expected to occur, doubling the number of attacks since 2020. Needless to say, regular security training tailored to your organization is necessary to build and sustain employee awareness and practical application. To achieve buy-in from your company, you need to fully embrace a culture of cybersecurity. Once employees know that a phishing email they open or a link they click could infect the entire network, they will be vigilant and take those extra seconds to pause and examine before acting.
#2 Email Security
Email is the most common form of online communication. It has been here since the start of the internet, and it is not going away. It is also cheap, if not free to use, which is one reason spam has been a problem for just about as long.
Utilize Spam Filtering
Spam started as a way for shady internet marketers to send ads to thousands of unsuspecting people at one time. Still, it wasn’t long before threat actors found it an easy way to phish personal data and deliver malware. Because of the human error we already mentioned, it is still one of the most common ways a cyber threat becomes a cyberattack. There is a simple, easy-to-implement, and cost-effective solution: spam filtering. Stop the threats before they even make it to an employee’s inbox. Spam filtering can detect unsolicited, harmful, and virus-infected emails and delete them before they become an issue. While this sounds incredible, it’s important to understand that this is not a full-proof method. The number of malicious emails sent daily is staggering, so employees must stay vigilant when a questionable email hits their inbox.
#3 Secure Authentication
It is hard to believe that only a few years ago, some authentication systems only required a seven or eight-digit password. This is no longer an option. Threat actors use tools that can crack weak passwords quickly, and your security policies must keep up.
This means you need to reassess and set policies on:
- Password length
- Password complexity
- Frequency of change
- Multifactor authentication (MFA)
Multifactor authentication means that even if a hacker cracks a password, they won’t be able to access an account without a secret code that is only sent to the owner’s phone number or email address.
Protect Your Organization Against Cyberattacks
Remote work is not inherently insecure, but let’s face it, for many organizations, neither is in-office work. The workplace, irrespective of your model, requires its own set of cybersecurity best practices. Being proactive with your cybersecurity strategy will prepare your organization for unforeseen threats in a highly digitized world. To learn more about safeguarding your organization, watch this informational webinar.
Let’s talk about your current concerns and challenges and how our Technology Advisory and Risk Management professionals can help address them.